watching nginx server status
Fri, 11/18/2011 - 16:48 — sandipOnce you have turned on nginx stub_status and enabled access from localhost:
location /nginx_status {
stub_status on;
access_log off;
allow 127.0.0.1;
deny all;
}You can now watch the the status realtime with:
watch -n1 'curl localhost/nginx_status 2>/dev/null'- sandip's blog
- Login or register to post comments
- Read more
Remove all messages from exim queue
Thu, 11/17/2011 - 16:39 — sandipexim -bp | awk '/^ *[0-9]+[mhd]/{print "exim -Mrm " $3}' | bash`exim -bp`, lists the messages in queue, which is piped through awk, printing to output "exim -Mrm {MessageID}" which is further piped into bash for execution.
ifconfig packet errors
Wed, 10/19/2011 - 09:26 — sandipIf "ifconfig" or "/proc/net/dev" shows you are getting packet errors and collisions, check that the network interface is not running at half-duplex. Full duplex would enable packets to flow in both direction in and out simultaneously.
ethtool eth0To turn on full duplex:
ethtool -s eth0 speed 100 duplex full autoneg offVerifying with `mii-tool eth0` should produce:
eth0: 100 Mbit, full duplex, link okMake this permanent by editing "/etc/sysconfig/network-script
ETHTOOL_OPTS="speed 100 duplex full autoneg off"- sandip's blog
- Login or register to post comments
- Read more
Apache LDAP Authentication and Require ldap-group
Wed, 10/05/2011 - 22:18 — sandipI was able to get htauth againt ldap and restricting against groups using:
<Location /protected>
# Ldap auth access
AuthType Basic
AuthName "Restricted"
AuthBasicProvider ldap
AuthzLDAPAuthoritative on
AuthLDAPURL "ldap://ldap.linuxweblog.
Require ldap-group cn=web,ou=group,dc=domain,dc=t
AuthLDAPGroupAttributeIsDN off
AuthLDAPGroupAttribute memberUid
</Location>Here is what the ldap search entry looks like:
# ldapsearch -x 'cn=web'
# extended LDIF
#
# LDAPv3
# base <> with scope subtree
# filter: cn=web
# requesting: ALL
#
# web, group, linuxweblog.com
dn: cn=web,ou=group,dc=linuxweblog
objectClass: posixGroup
gidNumber: 10002
cn: web
description: access to web protected folders
memberUid: user1
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1It is essential to enter "AuthLDAPGroupAttributeIsDN off" and "AuthLDAPGroupAttribute memberUid" for it to get to the member attribute.
Reference: mod_authnz_ldap
Check for fake googlebot scrapers
Wed, 10/05/2011 - 12:13 — sandipI noticed a bot scraping using fake GoogleBot useragent string.
Here is a one liner that can detect the IPs to ban:
$ awk 'tolower($0) ~ /googlebot/ {print $1}' /var/www/httpd/access_log | grep -v 66.249.71. | sort | uniq -c | sort -nIt does a case-insensitive awk search for keyword "googlebot" from apache log file removing IPs with "66.249.71." which belongs to google and prints the output in a sorted hit count.
You can validate the IPs with:
IP=66.249.71.37 ; reverse=$(dig -x $IP +short | grep googlebot.com) ; ip=$(dig $reverse +short) ; [ "$IP" = "$ip" ] && echo $IP GOOD || echo $IP FAKEReplace the IP value with the one you want to check.
- sandip's blog
- Login or register to post comments
- Read more
Remote install CentOS-6 on RAID10 using SOFIns boot disk
Wed, 09/07/2011 - 14:21 — sandipWhat if you needed to install Raid10 and CentOS-6 on a remote, unformatted server but had no way of accessing the server? You could try asking someone at the remote location to help you bootstrap the server, but that is not always possible. You could make an onsite visit, but that is undesirable. KVM-over-IP and IPMI are hardware solutions, but are expensive and require network setup.
This tutorial demonstrates how to access a remote, unformatted server in a fast, secure, simple and inexpensive way. It will show how to remotely provision the server with Raid10 and CentOS-6.
We will use a remote access service from SOFIns (www.sofins.com) to boot the remote computer and set up a secure tunnel for ssh and vnc access. We will need someone at the remote location to insert a SOFIns boot disk into this server, attach power and network and then turn it on. That is all they are required to do. We can do the rest remotely.
SOFIns works by booting the remote server with a live Linux operating system. SOFIns creates a VPN tunnel between the remote computer and a SOFIns' gateway. We use the gateway to log into the live Linux operating system that has booted the remote server.
Here are the procedures to set up Raid10 with a CentOS-6 on a remote server that we access via SOFIns.
Remote login via SOFIns gateway
-
Register and login to "sofins.com".
Once signed in, enter "SOFIns Controls" and click on the icon "+A" besides "Unassigned" to create a new boot disk agent.
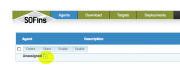 Select the checkbox besides the new agent that is created and click on the "Share" button.
Select the checkbox besides the new agent that is created and click on the "Share" button.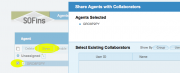 Enter email address of person to share the agent with and select "Offer assistance" tab and click "OK".
Enter email address of person to share the agent with and select "Offer assistance" tab and click "OK".This will send out the invite, where the client accepts and downloads the iso and boots the server off of the CD created from the iso.
Once the client boots up the remote server, it will show up under the "Targets" page.
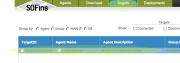 In The "Targets" page, click on the "Authorize Access" tab to "Enable" access and get the required ssh credentials to log in to the remote server via ssh.
In The "Targets" page, click on the "Authorize Access" tab to "Enable" access and get the required ssh credentials to log in to the remote server via ssh.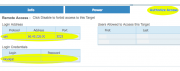 Login via ssh to the IP and port specified on the "Access" page.
Login via ssh to the IP and port specified on the "Access" page.
mysql repair tables
Thu, 09/01/2011 - 17:21 — sandipWith a recent OS upgrade, some of the mysql database tables got corrupted. Below is how I was able to get it repaired.
-
Stop mysql server.
Once mysql server is stopped, run a repair on all of *.MYI files via myisamchk:
# myisamchk -r /var/lib/mysql/*/*.MYIRun a mysqlcheck of all databases via:
# mysqlcheck -c --all-databases | tee /tmp/dbcheck.log# grep error -B1 /tmp/dbcheck.log | grep -v "error\|--" | sed 's/\(.*\)/REPAIR TABLE \1;/' >/tmp/dbrepair.sqlREPAIR TABLE database1.table1;
REPAIR TABLE database1.table2;
REPAIR TABLE database2.table1;# mysql> source /tmp/dbrepair.sql# mysqlcheck -c -e --all-databases- sandip's blog
- Login or register to post comments
- Read more
Install python-2.7 and fabric on CentOS-5.6
Fri, 08/05/2011 - 11:57 — sandipInstall the required packages first:
# yum install gcc gcc-c++.x86_64 compat-gcc-34-c++.x86_64 openssl-devel.x86_64 zlib*.x86_64Download and install python-2.7 from source:
$ wget http://www.python.org/ftp/pyth
$ tar -xvzf Python-2.7.2.tgz
$ cd Python-2.7.2
$ ./configure --with-threads --enable-shared
$ make
# make installLink the shared library:
# echo "/usr/local/lib" >>/etc/ld.so.conf.d/loca
# ldconfigVerify with:
$ which python
$ python -VInstall easy_install:
$ wget http://peak.telecommunity.com/
# python ez_setup.pyInstall fabric via easy_install:
easy_install fabricTo get the location of site-packages for current version of python:
$ python -c "from distutils.sysconfig import get_python_lib; print get_python_lib()"Delete trac tickets
Thu, 07/21/2011 - 15:41 — sandipTo delete trac tickets without installing extra plugins, here's the SQL.
Note: make sure to create a backup of trac.db first.
$ sqlite3 trac.db
delete from ticket_change where ticket = <TicketID>;
delete from ticket_custom where ticket = <TicketID>;
delete from ticket where id = <TicketID>;Replace "TicketID" with the ID of ticket that needs to be deleted.
To purge out all tickets, use the same sql without the where clause.
- sandip's blog
- Login or register to post comments
- Read more
auotmount shares for vzyum updates
Mon, 06/13/2011 - 10:08 — sandipNote: The directions at "http://wiki.openvz.org/Install
To share the vzyum cache directory between various containers. Edit "/etc/auto.master" to include the following:
/vz/root/{vpsid}/var/cache/yumInclude one line for each installed or planned VPS, replacing {vpsid} with the adequate value.
Then, create "/etc/auto.vzyum" file with only this line:
share -bind,ro,nosuid,nodev :/var/cache/yum-cache/shareRestart the automounter daemon.
Edit "/vz/template/centos/5/x86_64/
cachedir=/var/cache/yum-cache/Create the corresponding cachedir:
mkdir /var/cache/yum-cache/shareTest with:
vzyum {vpsid} clean allThis should create all of the yum cache directory at "/var/cache/yum-cache/share" location and should be available to the openvz container via bind mount.